ELMhub
ENGAGE:
employees, contractors; remote or in-office
CONNECT:
workflow, applications, third party services
SHARE:
policies, user guides, knowledge & insights






employees, contractors; remote or in-office
workflow, applications, third party services
policies, user guides, knowledge & insights






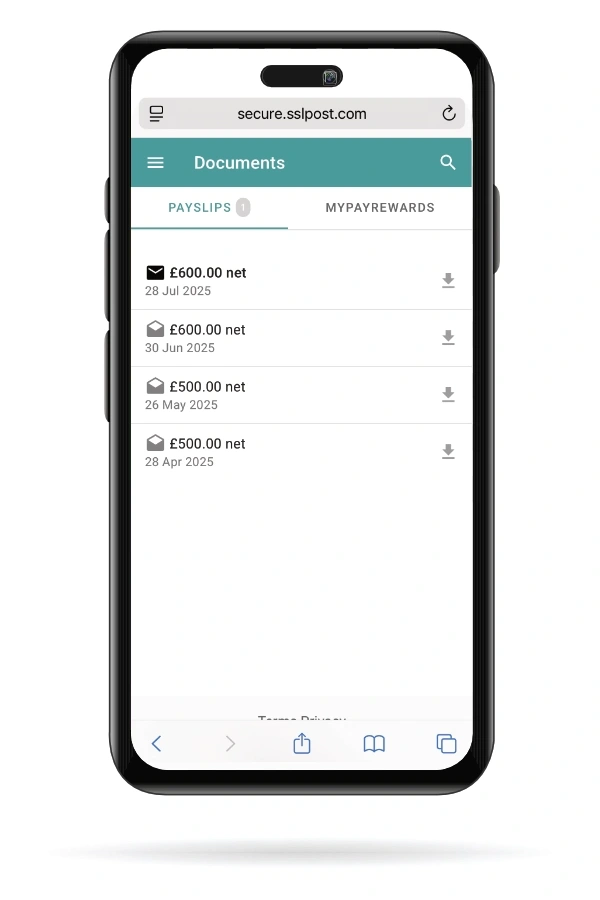
For those who just need the basics
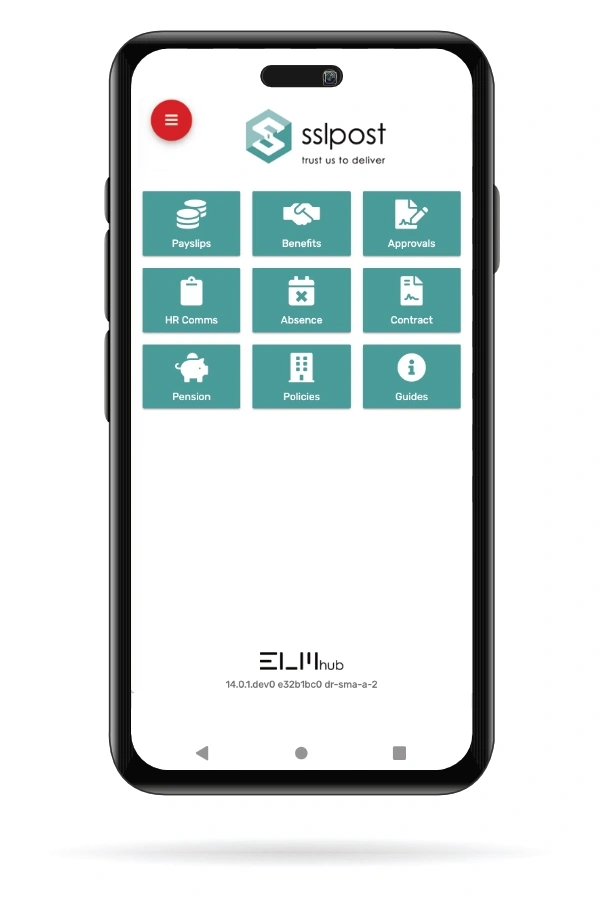
For multiple ELM applications; fresh, clean and easy to read
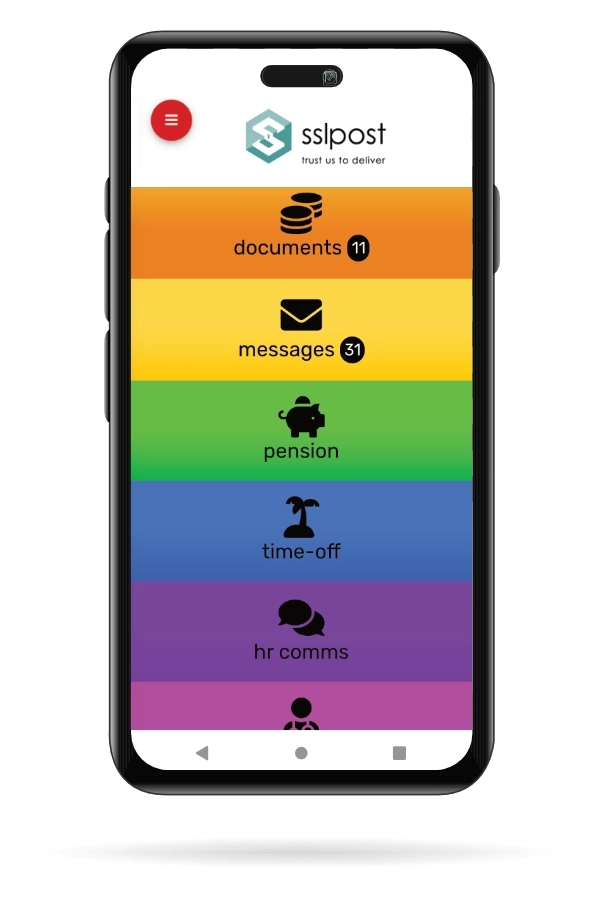
For multiple ELM applications; SEND & ESL-friendly













Securely upload confidential, time critical, personalised or non-personalised documents to single or multiple recipients – 100% delivery assured.
Create secure libraries and repositories for operations, contracts, employee handbooks & policies, planning & development, pensions, legal & human resources, training & personal development, to name just a few.
Add SSLPost esign for those documents requiring agreement or approval.



















Gain instant access to a suite of industry-leading whitepapers that reveal how Conscious Business Lifecycle Management can transform your operations, elevate employee experience, and maximise long-term value.
Click on the whitepaper and complete the short form to gain access to all five whitepapers.
Each resource offers practical guidance, expert insight, and proven strategies – available exclusively to verified professionals.
Exclusive resources for forward-thinking organisations
Gain insights from our latest whitepapers — crafted to help you lead, adapt, and grow. Explore proven strategies, expert perspectives, and practical guidance.
